“Investment in your future”

The project “Secure and Privacy Protecting Pandemic Tracking Platform” was co-financed by the European Union through the European Regional Development Fund.
The System Security Lab focuses on a wide range of topics in field of cybersecurity and privacy, especially on those topics that affect our citizens.
Since January 2020, we have been investigating the security and privacy aspects of the Contact Tracing apps worldwide and in particular the Corona-Warn-App (CWA) used in Germany. CWA is based on Google & Apple Exposure Notification interface (GAEN).
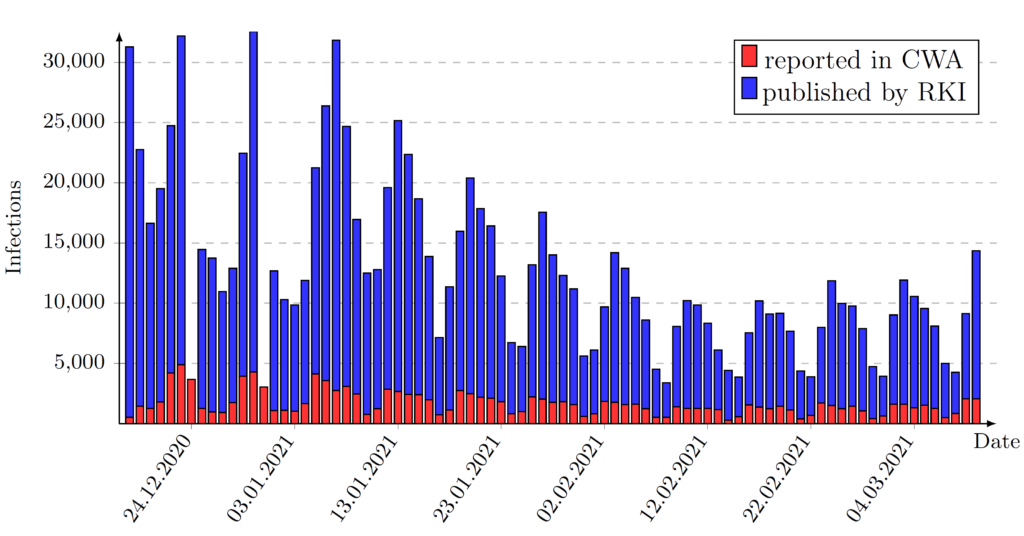
Our team has collected more data on the use of the CWA and the new field experiments again confirm security and privacy gaps. The experimental setup is relatively simple: commercially available and inexpensive ESP32 microcontrollers equipped with Bluetooth and Wi-Fi were converted by the students into so-called “sniffers”.
The battery-powered sensors were placed weatherproof in downtown Darmstadt, in traffic hubs, parks and supermarkets. For several weeks, the sensors collected various data: MAC addresses, and Rolling Proximity Identifiers, or RPIs, the random IDs sent by the Corona warning app via Bluetooth Low Energy. In addition, the corresponding times were collected.
More than theory – Tracking in “the wild”
More than 21,000 collected MAC addresses were used to obtain information about the Corona-Warn-App (CWA) “hotspots” in Darmstadt, as the heatmap shows.
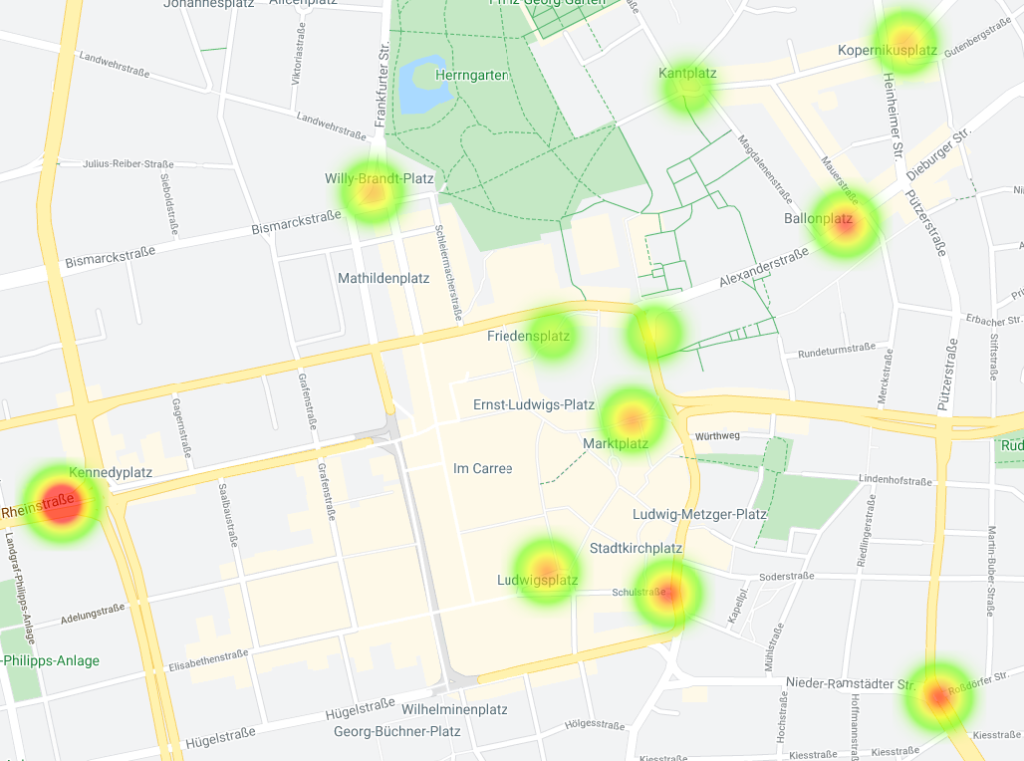
By analyzing the data generated at the points of interest, we demonstrate in the wild that tracking infected users (of the CWA) is possible and not only a theoretical attack. The installed sensors recorded all RPIs that passed by and provided them with the corresponding time stamp. During the experiment between mid-December 2020 and early March 2021, over 97,000 unique RPIs were collected.
Temporary Exposure Keys (TEK), the so-called daily keys generated by the smartphone every 24 hours, were also used to evaluate these unique RPIs. Using cryptographic algorithms and various calculations, starting from a total of 17 Temporary Exposure Keys (TEK) uploaded to the CWA server due to a positive test result, we could precisely assign some of the RPIs among the collected RPIs. Although this is a one-way cryptographic function, enough “sniffing” sensors, which additionally contain the location data, could be used to track infected CWA users. In addition, the collected data also allowed conclusions about the used end device and its operating system.
Linking RPIs – tracking a person’s movements
Another case study demonstrate that the Corona-Warn-App is also vulnerable “in the wild” to the “Little Thumb Attack” published in July 2020 for SwissCovid. The Swiss researchers have demonstrated that user of the SwissCovid app could be tracked if the MAC address and the RPI did not update at the same time, but with a time delay. These overlapping updates lead to so-called “Pebbles”, i.e. faulty Bluetooth messages that enable linking of the user RPIs over a certain period of time. Such “Pebbles” could be detected in our real-world scenario. It was possible to track a user through such a Pebble across two sensors. This was only possible because this vulnerability exists in the Exposure Notification of Google and Apple (called GAEN), although it should not exist.
If the MAC address and RPI change synchronously, it is not possible to link the data. Using so-called callbacks, i.e., via the operating system, the CWA is informed that the MAC address has changed, so that the RPI can also update. Based on the data recorded, it seems that this is implemented variously in different devices, so not all smartphones are affected to the same extent. While there is a callback in iOS operating systems, nine out of ten Android devices tested parallel in the lab had no such callback. Even though the Android devices tested in the lab could not generate complete “Pebbels”, parts of “Pebbels”, so called “Overlaps” were recorded.
Hardly any protection against security vulnerabilities
The results show that the previously theoretical research approaches to various security vulnerabilities of the CWA could be shown in the wild, using simple, commercially available and low-cost sensors. It was possible to track the movement profiles of infected users, e.g., in the supermarket, for a certain period of time. Despite many updates, Google and Apple have not managed to fix the vulnerabilities yet.
